Network Security System

Discover More Now
Amar Enterprises: Cutting-Edge Network Security System Solutions
In today’s digital age, safeguarding your network infrastructure is paramount. Amar Enterprises is your trusted partner for comprehensive network security system solutions. With a commitment to excellence and a keen understanding of the ever-evolving cybersecurity landscape, we provide robust, reliable, and tailored security measures to protect your organization from cyber threats.
- Comprehensive Security Solutions
- Customized Security Strategies
- Compliance and Regulatory Adherence
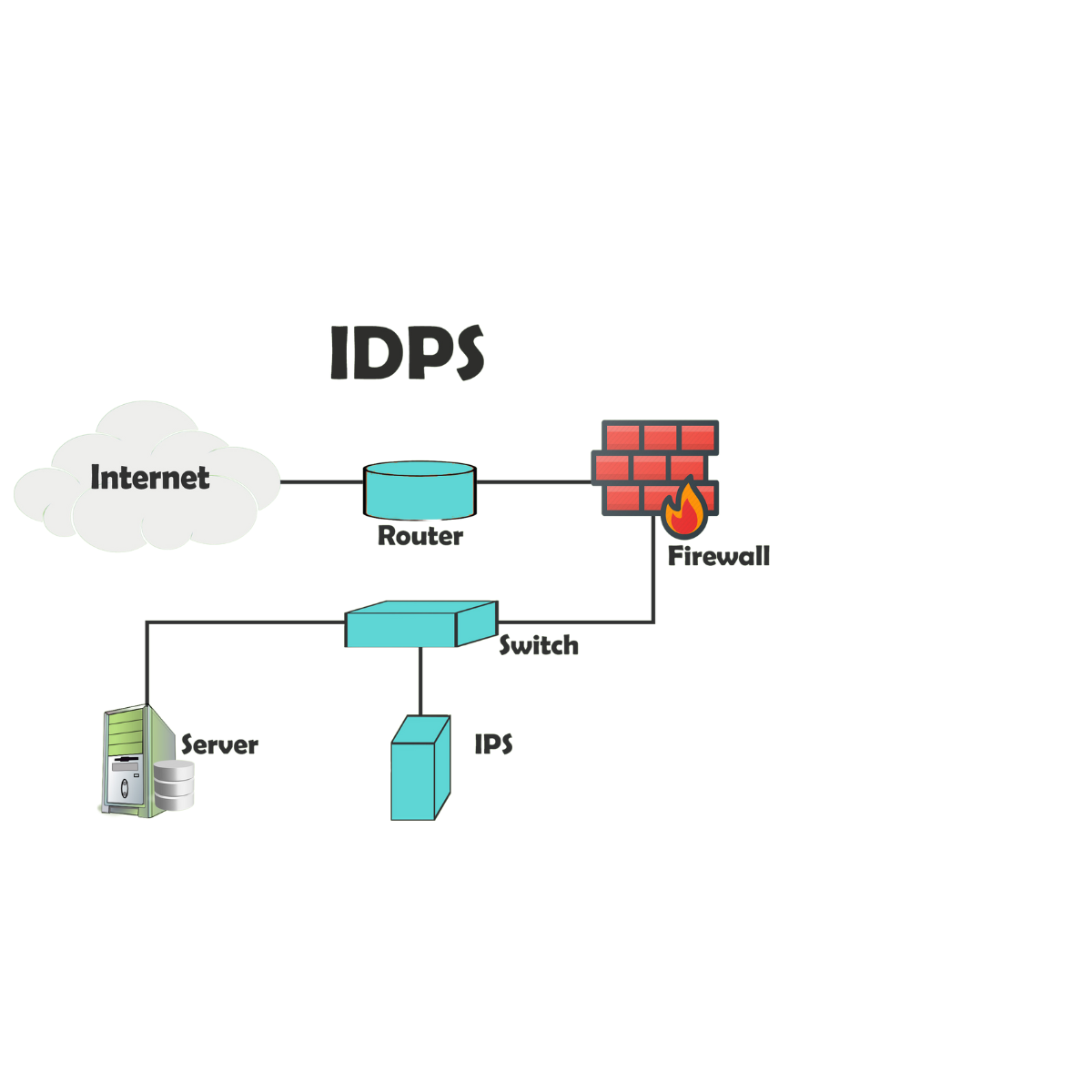
Intrusion Detection and Prevention Systems (IDPS)
Our IDPS solutions monitor network traffic for suspicious activity and take proactive measures to prevent intrusions.Go beyond basic signature matching to leverage behavioral analysis. This helps identify zero-day attacks and other novel threats that haven't been defined yet.

Security Audits and Assessments
Data backup refers to the process of creating copies of your essential data on a regular basis. This data can include everything from financial records and customer information to documents, emails, and marketing materials. Data recovery involves restoring this backed-up data in case of accidental deletion, hardware failure, cyberattacks, or natural disasters.

Encryption
Encryption techniques protect sensitive data by converting it into an unreadable format that can only be decrypted by authorized users. This ensures that even if data is intercepted during transmission, it remains inaccessible to unauthorized parties.


We Do More For Your Business
"Your Shield Against Cyber Threats, Network Operations 24/7."
Firewall Protection: Firewalls serve as the first line of defense by monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. They help block unauthorized access and filter potentially harmful data from entering the network.
Regular Security Audits and Assessments: Conducting periodic security audits and assessments helps identify vulnerabilities and potential security gaps within the network. This proactive approach allows organizations to address issues before they can be exploited by cybercriminals, ensuring ongoing network security.
Technology Path
Trusted IT Solution & Service Company
Experienced
10 years of experience
Convenience
Support any time 24/7
Professional
Take our job seriously
Amar Enterprises provides comprehensive IT security services, including network security, data encryption, cybersecurity audits, incident response, and managed security solutions.
Newsletter
Contact
- Office Timings
- Mon - Sat: 9.30 am - 6.30 pm
© All Copyright 2024 by amarenterprisestech.com
